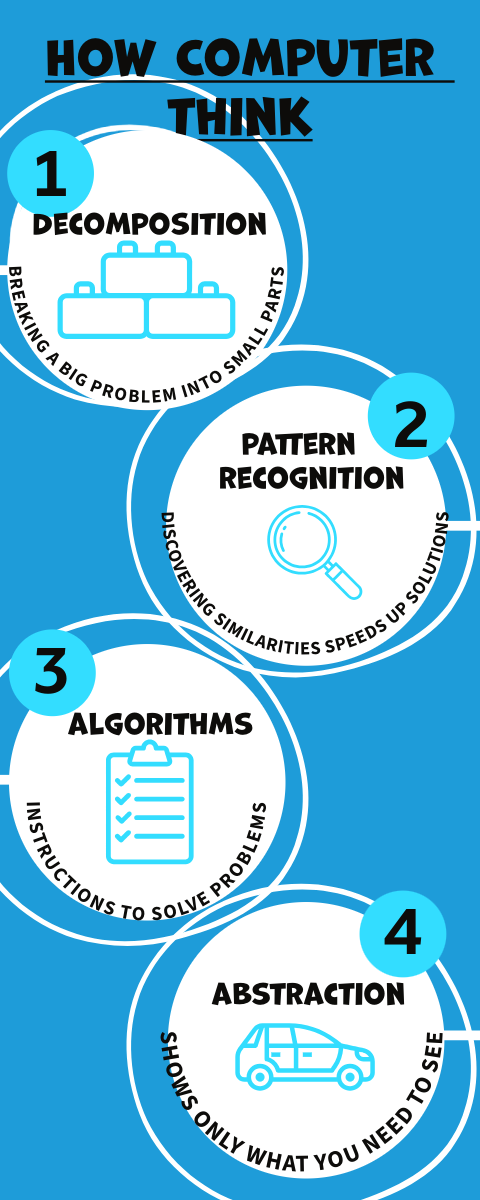
L03: Computing Concepts
L03: Reflection
This lesson made me think about how much humans can adapt both physically and mentally to new challenges. Physically,people create tools, machines, and technology to make up for our natural limits. Mentally, we adapt by learning new skills, solving problems, and figuring out better ways to do things. It showed me that a lot of human progress comes from finding ways to work smarter, not just harder. Technology and knowledge let us push past the limits we were bornwith, and that’s what really drives growth and change.
L03: Data Analytics
From the reading within Zybooks what I found most confusing is the word choice for ‘prescriptive’. Overall, though I understand the definitions for all three. For instance, lets say you want to know the number of student who take out student loans and the amount they take out. You would take that data and look for insight within that data like why do the amounts vary. From that data we can make predictions. This is predictive analysis. From those predictions it tells us what should be done to get a specific outcome. That is prescriptive analysis.
L02: History and Basics
L02: Reflection
This lesson gave me a better understanding of how computers have evolved over time. We looked at the basic history ofcomputers, starting from early mechanical devices to the powerful machines we have today. It’s crazy to think about how far things have come in just a few decades. We also talked about some of the major figures who made huge contributions to computer science, like Charles Babbage,Ada Lovelace, Alan Turing, and others. Learning about them made me realize that a lot of what we use today started with simple but powerful ideas from people who thought way ahead of their time.
L02: Binary Number Game
I had very little trouble converting the numbers as I had to use this extensively in subnetting and creating networks in my previous job as an IT Project Manager. Binary representation is the foundation of digital computing. Computers do not understand decimal like humans. Instead, they rely on using binary which consists of only two digits: 0 and 1. Each bit represents a power of 2, and multiple bits together create numbers, characters, and even complex data structures. From this we can extrapolate how computers process data and that all storage is stored in binary. Even text is represented in ASCII or Unicode, where characters are mapped to binary values. URLs are converted using a protocol
Penjee. (n.d.). Binary numbers game. Penjee. https://games.penjee.com/binary-numbers-game/
L02: Binary Statement
Hello
This is a binary code
I love data
I group the binary into 8-bit chunks for easy conversion and checked the ASCII table for the corresponding decimal amount and found the associated character. Help to understand how machines are able to translate the 1 and 0 into human-readable data and vice versa. No real challenge since I have done this before. It reinforces the fundamental idea of how computers work from just 1 and 0s.
Introduction to Information Technology
L01: Reflection
This lesson helped me understand what an information system really is — it’s not just a computer or a program, it’s the combination of people, hardware, software, data, and processes working together to manage and share information. It made me realize that the human side is just as important as the technical side. We also went over the System Development Life Cycle (SDLC), which showed me that building any system isn’t just aboutcoding. It’s a full process with steps like planning, designing, testing, and maintenance. Skipping steps can cause big problems later. We reviewed cloud computing apps again, like Google Drive and Dropbox, and how they make it easier to store and access files from anywhere. It’s crazy how much easier working across devices has gotten because of the cloud. Another thing we talked about was how using computers can affect your health. Sitting too long, bad posture, and too much screen time can cause real issues if you’re not careful. It made me think about taking breaks and setting up my workspace better.
L01: Virtual Information Treasure Hunt
References
Bettis-Outland, H. (2011). Decision-making’s impact on organizational learning and information overload. Journal of Business Research, 64(6), 509–515. https://doi.org/10.1016/j.jbusres.2010.12.021
This peer-reviewed paper examines the intricate relationship between decision-making, organizational learning, and information overload. There is a key emphasis on policy, business, and political making decision, going into detail how decisions are derived. Incremental decision-making involves small, gradual steps with minimal organizational change, while comprehensive decision-making considers all possible scenarios, leading to significant shifts in procedures and traditions. Published in the Journal of Business Research—a reputable academic database—the study provides insight into how excessive information impacts decision-making and organizational learning.
Gursoy, D. (2019). A critical review of determinants of information search behavior and utilization of online reviews in the decision-making process. International Journal of Hospitality Management, 76(B), 53–60. https://doi.org/10.1016/j.ijhm.2018.06.003
This peer-reviewed study looks at a variety of factors, such as information overload, that influences how consumers process and utilize online reviews during their decision-making process. A keynote, however, is this study highlights the less-explored aspects such as information overload, confusion, presentation format, trust, and evaluation mode, alongside the impacts of perceived risk and familiarity. Published in the International Journal of Hospitality Management—it examines the possible influences on consumers decision-process.
Hafiz Muhammad, B. F., Zulfiqar, S., Noor, S., & Huo, C. (2022). Examining multiple engagements and their impact on students’ knowledge acquisition: the moderating role of information overload. Journal of Applied Research in Higher Education, 14(1), 366-393. https://doi.org/10.1108/JARHE-11-2020-0422
This peer-reviewed paper explores how students gather information and its impact on knowledge acquisition, with a particular focus on the role of information overload. The author questions whether the abundance of knowledge is a double-edged sword—offering vast resources while simultaneously making it harder to filter and comprehend relevant information. Published in the Journal of Applied Research in Higher Education—it sheds light on the impact of information overload in diverse educational settings.
Sbaffi, L., Walton, J., Blenkinsopp, J., & Walton, G. (2020). Information overload in emergency medicine physicians: A multisite case study exploring the causes, impact, and solutions in four North England National Health Service Trusts. Journal of Medical Internet Research, 22(7), e19126. https://doi.org/10.2196/19126
This scholarly article looks at the growing influence of digital technologies in emergency medicine and their role in contributing to information overload—affecting patient care. This issue is especially critical in emergency medicine, where the overwhelming flow of information can impact patient care. Understanding its causes, effects, and management strategies is essential to alleviating stress in the profession. Published in the Journal of Medical Internet Research, this study offers relevant findings for broader applications in information overload research.
L01: Introduce Yourself and Explain What Interests You Most in IT
Good evening everyone!
My name is Mickey Blair. I’m coming from San Diego, CA. I’m a Freshman studying cybersecurity. The IT discipline that appeals most to me is Information Technology as cybersecurity is an emerging focus that branches off from IT its critical to understand the user, the environment, and the security needs of both. My technical strength is identifying possible intrusions within a network and understanding how to correlate data to provide insights into threats. Well-versed in computer hardware and comfortable being in the CLI of a Linux or Windows machine. My weakness is programming as I’m taking two programming classes this semester. IST242 and CMPSC131 to improve my understanding of various languages. Ultimately, I want to become a pen-testing consultant and based on my experiences in my prior internship I know it will be an uphill battle as it requires you to understand various environments quickly. I don’t see AI taking away many cybersecurity jobs mainly because we can extract meaning out of data and correlate various pieces of data that AI has yet to mimic. I’ve seen AI implemented in companies however, false positives abound because it flags everything that could be a ‘threat’. We as analysts know the environment and can comb through and find where the real threats are.
Hello World
Welcome to Hexo! This is your very first post. Check documentation for more info. If you get any problems when using Hexo, you can find the answer in troubleshooting or you can ask me on GitHub.
Quick Start
Create a new post
1 | $ hexo new "My New Post" |
More info: Writing
Run server
1 | $ hexo server |
More info: Server
Generate static files
1 | $ hexo generate |
More info: Generating
Deploy to remote sites
1 | $ hexo deploy |
More info: Deployment